Washington, DC - An Adware strain name Zacinlo is wreaking havoc on US-based Microsoft Windows 10 users. If you’ll remember when it was forced upon us released back in 2015, one of the biggest selling points of Windows 10 was that it featured improved security that was specifically purposed to make it harder for root kits to gain a foothold over the newly minted OS.
Well, here we are three short years later BitDefender has discovered Zacinlo, an adware strain that uses a RootKit component to achieve persistence across OS reinstalls. Granted, RootKit exploits are old news for more dated versions of Windows, but this strain even works on Windows 10. In fact, BitDefender found that nine out of ten victims were using Windows 10, leading them to assume the strain was developed specifically to target Windows 10 users.
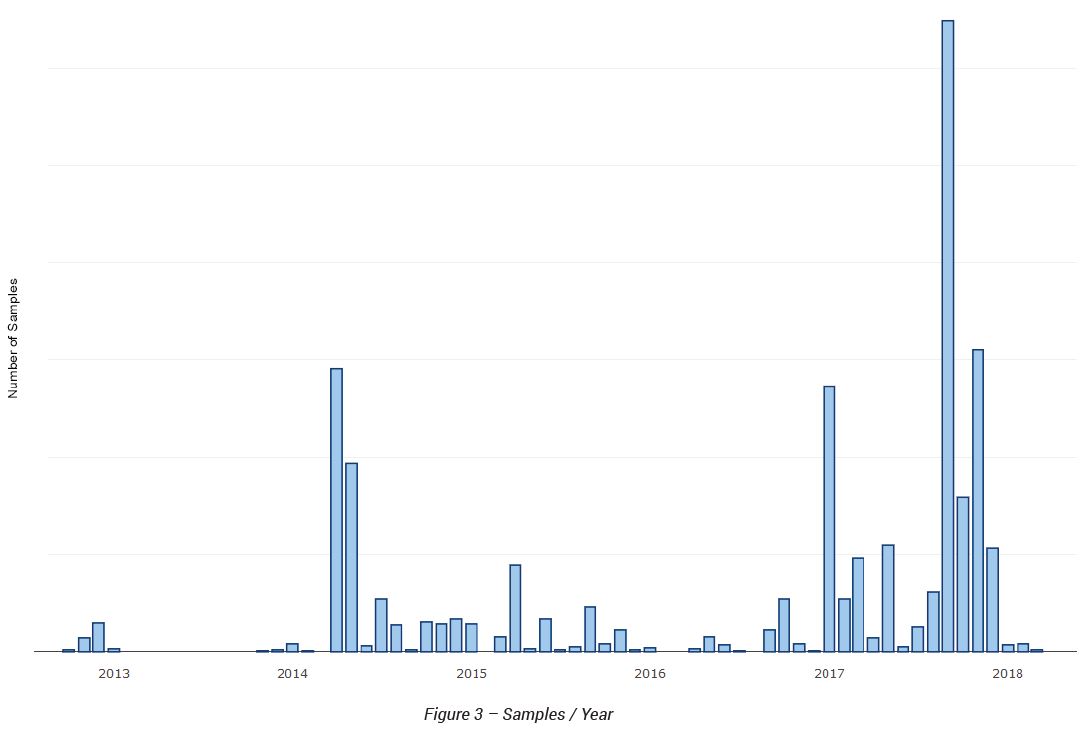
The group behind Zacinlo has been actively distributing malware since 2012, though it only appears to have learned how to target Windows 10 users within the past two years. Its longevity doesn’t mean the group has been releasing malware at a steady pace though, rather it has ebbed and flowed with large flourishes in 2014 and 2015 as well as in 2017 and 2018.
How does Zacinlo infect Windows 10 users?
By using the old bait-and-switch. Users think they’re downloading a Virtual Private Network (VPN) client, what they’re really getting is infected.
The adware components are silently installed by a downloader that is presented as a free and anonymous VPN service (s5Mark), distributed in an installer. s5Mark has a simple graphical interface used as a decoy for the intrusive unwanted behavior taking place behind the scenes. Note that a non-technical user is led to believe that a VPN connection is established even though no such thing is even attempted.
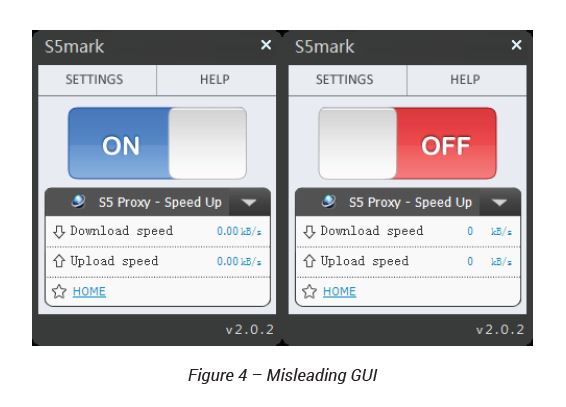
For all intents and purposes the VPN part of the app is a total dud, but it does accomplish its primary goal: installing the RootKit on your system.
A RootKit is critical to the adware because it can ensure that Zacinla survives on the host for as long as it needs to.
[The RootKit] is responsible for providing persistence and protection for the other components from being read, written or deleted. It is also used to patch or block antimalware services.
Specifically, the RootKit can block anti-malware solutions from:
- BitDefender
- QiHoo
- Kingsoft
- MalwareBytes
- Symantec
- Panda
- HitmaPro
- Avast
- Avg
- Microsoft
- Kaspersky
- Emsisoft
- Zemana
The RootKit finds the solutions by their file names or by using the subject field name on their certificates, then it prevents them from ever starting in the first place.
Zacinlo is not a one-trick pony
In addition to its RootKit, Zacinlo also knows a few other tricks. One that we’re well acquainted with is Man-in-the-Middle attacks. Zacinlo can intercept HTTPS connections and eavesdrop on or manipulate traffic. Right now Zacinlo is primarily using that functionality to inject ads. But it certainly stands to reason that the feature can be exploited for more nefarious ends.
Beyond that, jealousy is also an issue. Zacinlo can identify and delete other, competing adware. It can also run a headless version of Google Chrome where it loads web pages and clicks on things so that the hackers behind it can generate money.
It also collects a lot of information about you and the way that you use your computer. It can even take screenshots.
“This functionality has a massive impact on privacy as these screen captures may contain sensitive information such as e-mail, instant messaging or e-banking sessions.”
Best of all, Zacinlo can update itself, adding features along the way to make it even more intrusive and creepy.
How do I get rid of Zacinlo?
This is a good way to test your antivirus/anti-malware solution in a trial by far.
“Since the rootkit driver can tamper with both the operating system and the anti-malware solution, it is better to run a scan in this rescue mode rather than running it normally.”
That’s right, start your machine up in Rescue Mode, Safe Mode, whatever you kids call it these days and then run your security program. If it can identify it, you should be able to delete it and move on with your life.
If it can’t, maybe find a new security solution.
