Washington, DC - One story that got lost in the torrent of national news last week was Microsoft shutting down six phony websites created by a group affiliated with the Russian government. The six websites were created to mimic websites related to public policy institutes and the US Senate. The Russian hackers were attempting to steal credentials and potentially infect the computers of anyone that tried to access the sites.
“The effort by the notorious APT28 hacking group, which has been publicly linked to a Russian intelligence agency and actively interfered in the 2016 presidential election, underscores the aggressive role that Russian operatives are playing ahead of the midterm elections in the United States,” writes Elizabeth Dwoskins of the Washington Post. “U.S. officials have repeatedly warned that the November vote is a major focus for interference efforts. Microsoft said the sites were created over the past several months and that the company was able to catch them early, as they were being set up. It did not go into more specifics.”
APT28 is also known as Fancy Bear.
While Microsoft reports that the websites were not used in an attack, these kinds of sites can be used for spear-phishing and as malware carriers. Spear-phishing is a highly specialized form of phishing where the attacker conducts surveillance and socially engineers an email that looks and feels authentic enough to get the recipient to take an intended action, in this case following a link and logging into a website.
APT28 targeted:
- The Hudson Institute, a conservative Washington think tank actively investigating corruption in Russia. (my-iri.org)
- The International Republican Institute, a non-profit group that promotes democracy around the world. (hudsonorg-my-sharepoint.com)
- The US Senate, with three different websites that appeared to be affiliated with Congress’s upper chamber. (adfs-senate.service; adfs-senate.email; adfs.senate.group)
- Microsoft itself, with a website that spoofed the company’s own online products. (office365-onedrive.com)
It’s clear Fancy Bear was primarily targeting Microsoft users. Obviously, you have the fake Microsoft website, which is a pretty big indicator itself, but ADFS is an acronym that stands for Active Directory Federation Services, which is a single sign-on solution made by Microsoft.
The way Microsoft took down the sites is fairly interesting. It used a legal maneuver that it has employed over a dozen times since 2016 to disable 84 sites run by APT28. It obtains a court order that legally enables it to transfer the malicious domains to its own servers where it can effectively shut them down and study them. Microsoft has also used this tactic to shut down botnets. Last Monday’s court order was executed in Virginia.
Now, there are a lot of political and legal implications that stem from Microsoft shutting down these websites. But we’re going to focus on one very specific point: website identity.
The fake Russian websites all used DV SSL certificates
Let’s preface with this: we are not criticizing Domain Validation SSL certificates here. We are simply observing the conditions that enabled these websites to look more legitimate. All six used DV SSL certificates, which allowed the websites to receive a “Secure” tag in the address bar of most desktop browsers, while giving it the traditional green padlock indicator on mobile browsers.
We’ve made no secret of our distaste of the current DV security indicators. And to its credit, Google seems to have come to its senses and will be removing positive indicators for websites that have DV SSL installed in the next few updates of its Chrome browser.
Let’s take a look at the six certificates in question:
| Domain | Certificate FQDN: | Issued On | Verification | Details |
| hudsonorg-my-sharepoint.com | hudsonorg-my-sharepoint.com | Mar 22, 2018 | Domain Validated | https://crt.sh/?id=372250509 |
| office365-onedrive.com | office365-onedrive.com | Apr 25, 2018 | Domain Validated | https://crt.sh/?id=419954326 |
| senate.group | adfs.senate.group | Jun 27, 2017 | Domain Validated | https://crt.sh/?id=305392600 |
| my-iri.org | sharepoint.my-iri.org | Apr 16, 2018 | Domain Validated | https://crt.sh/?id=399462567 |
| adfs-senate.services | No certificate found* | |||
| adfs-senate.email | No certificate found* |
Information on two of the six certificates was not available, possibly because they were issued before the requirement for CAs to publish every issuance into a Certificate Transparency log, which makes them harder to track down.
I wouldn’t call it a problem, because according to many around the industry it’s more of a feature than a bug, but DV SSL offers a complete lack of identity information. It does authenticate a server, which as many critics of business authentication certificates will tell you, is exactly what it’s supposed to do.
But let’s be honest, to the average internet user server authentication is absolutely meaningless. Here’s the identity information included in the four logged certificates:
| Subject Name: commonName = hudsonorg-my-sharepoint.com organizationalUnitName = Free SSL organizationalUnitName = Domain Control Validated |
| Subject Name: commonName = adfs.senate.group organizationalUnitName = Free SSL organizationalUnitName = Domain Control Validated |
| Subject Name: commonName = office365-onedrive.com organizationalUnitName = Free SSL organizationalUnitName = Domain Control Validated |
| Subject Name: commonName = sharepoint.my-iri.org organizationalUnitName = PositiveSSL organizationalUnitName = Domain Control Validated |
None of that helps a user discern a fake website from a legitimate one, especially when the browser is telling you it’s secure.
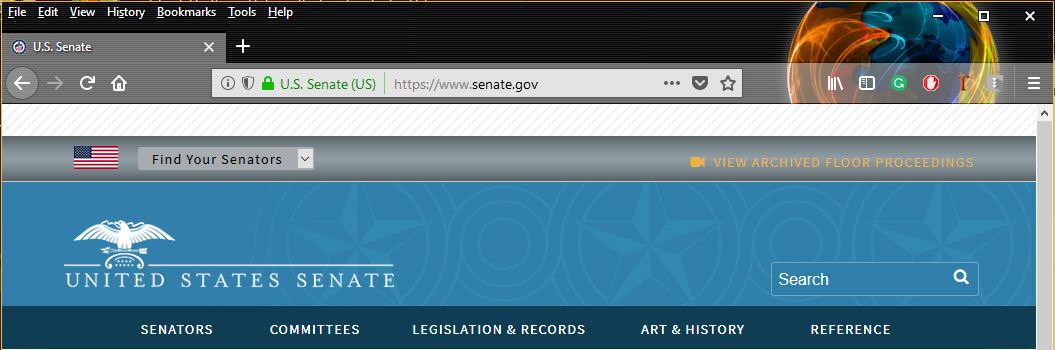
Fortunately, the US Senate website has an Extended Validation SSL certificate. Extended Validation SSL certificates have one major advantage over their Organization Validation and Domain Validation counterparts: they carry a unique visual indicator that places your organization’s name in the address bar beside the URL.
Here’s a look at the Senate’s EV indicator:
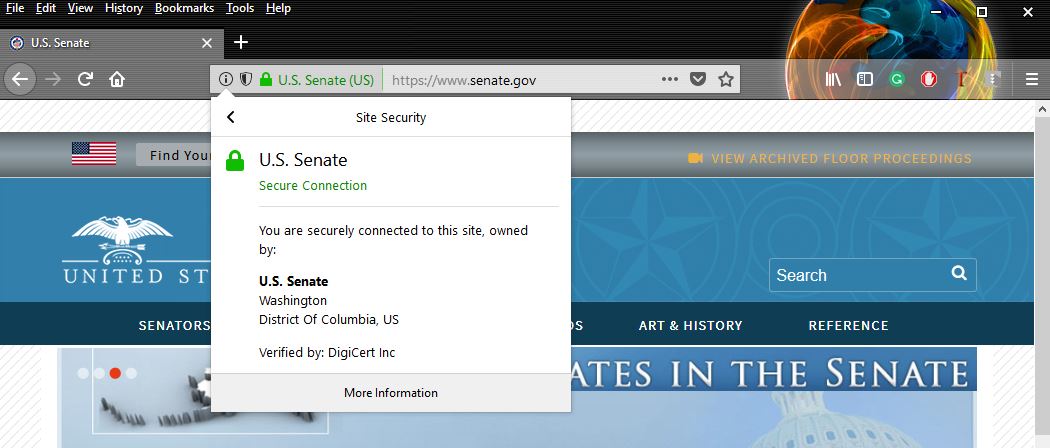
And here’s the identity information that can be found by clicking the EV indicator (Firefox does this better than any other browser):
And of course, if you click and ask for more information, you can see the full certificate details:
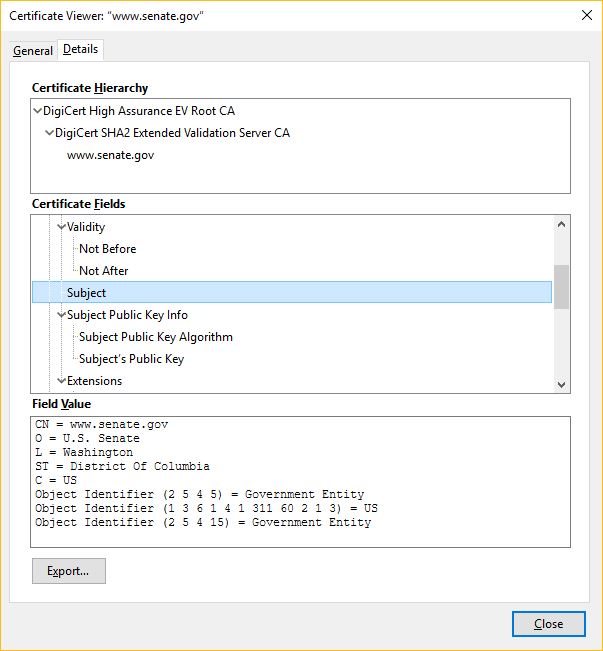
Again, nobody does this better than Mozilla, who makes information easily accessible to its users.
So where are we going with this?
All public-facing government websites should have an Extended Validation SSL certificate
The APT in APT28 stands for “Advanced Persistent Threat,” and that is painfully apropos of our current national cybersecurity landscape. There are highly sophisticated, state-backed cyber terrorists (let’s call them what they really are) actively waging digital campaigns to subvert our national institutions and influence our elections and general discourse.
That’s why every public-facing government website, from the smallest municipalities all the way up to the largest federal institutions, needs to have an EV nameplate beside their URL in browsers’ address bars. This is one of the most direct ways for websites to assert their identity to their visitors. It’s unmistakable, it’s unfakeable and it reflects that the organization has been thoroughly vetted by a trusted Certificate Authority.
 Now, I already know there are some objections percolating in the minds of EV critics. And that’s fine. EV isn’t perfect. Everyone agrees we can do more to strengthen the validation aspect of EV and we need to do something about EV collisions.
Now, I already know there are some objections percolating in the minds of EV critics. And that’s fine. EV isn’t perfect. Everyone agrees we can do more to strengthen the validation aspect of EV and we need to do something about EV collisions.
But in this context, when talking about public-facing government websites, and even some think tanks and institutes, those objections really don’t apply. There shouldn’t be any name collisions and verifying that a government entity is indeed a government entity is a pretty straightforward process.
More to the point, people need that identity information to be there more than ever. And while you might be tempted to point out that not everyone knows to look for it—that can be corrected with education.
Also, when is removing someone’s access to information ever the right call? How is that in the public interest?
Extended Validation SSL certificates give people across the world the ability to confirm the authenticity of a government website with just a single glance. That’s why all public-facing government websites need EV SSL. Not just in the US, but all around the globe.
Identity has never been more important than it is right now.
